WebSockets Unveiled: A Deep Dive for Developers and Penetration Testing Engineers
Introduction
The modern web thrives on real-time interaction. From collaborative tools like Google Docs to multiplayer gaming and live customer support, users today expect seamless, instantaneous communication. Traditional HTTP is ill-suited for such scenarios due to its stateless and request-response nature. This is where WebSockets shine.
For developers, WebSockets offer a powerful tool to establish persistent, bidirectional communication between clients and servers. For penetration testing engineers, however, this power poses novel security challenges that cannot be ignored.
In this article, we take an exhaustive tour of WebSockets—dissecting how they work, how to implement and secure them, and most importantly, how adversaries exploit them. We strictly follow British English conventions and speak to both technical implementers and C-level decision-makers, focusing on business impact, ROI, and risk mitigation.
1. What are WebSockets?
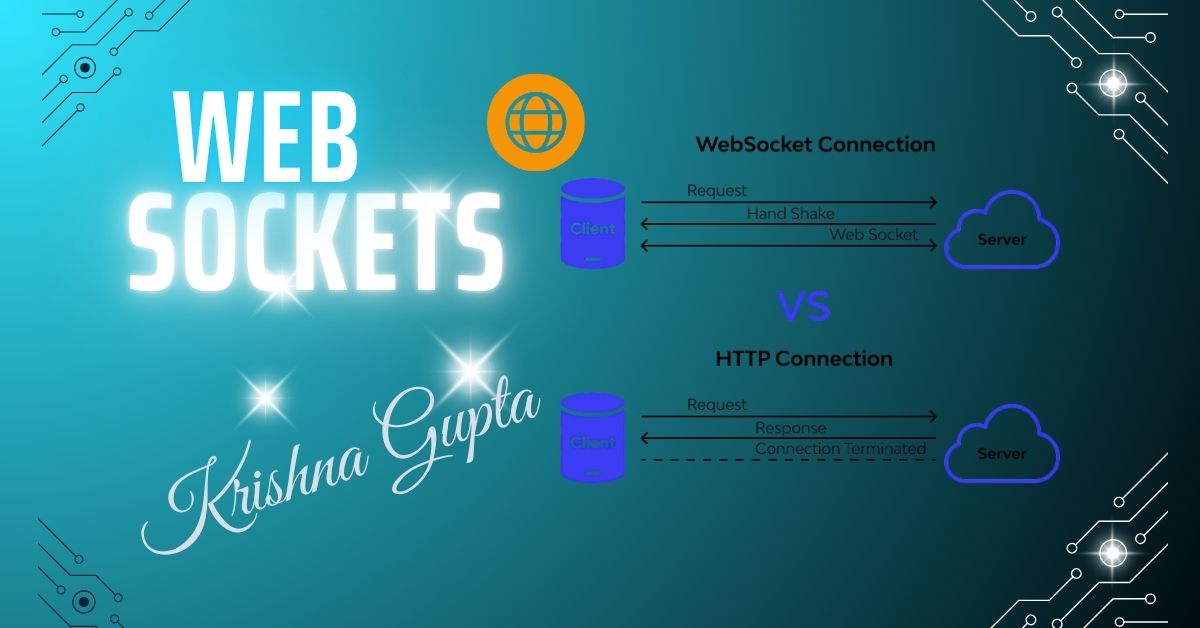
WebSockets are a protocol providing full-duplex communication channels over a single TCP connection. Defined in RFC 6455, WebSockets allow clients and servers to exchange data at any time, unlike the request/response model of HTTP.
Key Characteristics:
- Persistent connection
- Bidirectional communication
- Low latency
- Lightweight header frames
- Operates over port 80 (HTTP) and 443 (HTTPS)
How It Differs from HTTP:
| Feature | HTTP | WebSocket |
| Communication | Unidirectional | Bidirectional |
| Connection | Stateless | Stateful |
| Latency | Higher | Lower |
| Protocol Overhead | High | Minimal |
| Use Case | Traditional web apps | Real-time apps (chats, stock tickers) |
2. WebSocket Lifecycle: From Handshake to Termination
A. Initial Handshake
The WebSocket connection begins with a standard HTTP request:
GET /chat HTTP/1.1
Host: server.example.com
Upgrade: websocket
Connection: Upgrade
Sec-WebSocket-Key: dGhlIHNhbXBsZSBub25jZQ==
Sec-WebSocket-Version: 13
B. Server Response
If the server supports WebSockets, it replies:
HTTP/1.1 101 Switching Protocols
Upgrade: websocket
Connection: Upgrade
Sec-WebSocket-Accept: s3pPLMBiTxaQ9kYGzzhZRbK+xOo=
After this upgrade, the communication becomes persistent and bidirectional.
C. Data Frames
Communication now takes place in frames (text, binary, ping/pong, close frames).
3. Use Cases of WebSockets in Business
1. Fintech Platforms
Live stock market updates, bid/ask prices, and trade feeds rely on WebSockets for sub-millisecond updates.
2. Customer Support
Live chat tools use WebSockets to reduce latency and ensure smooth user experience.
3. IoT & Smart Devices
Sensor data transmission and remote device control depend heavily on real-time communication.
4. Gaming and Multiplayer Apps
Synchronising game states, player positions, and chat functions rely on WebSockets for immersive UX.
4. WebSocket Security: A Double-Edged Sword
While WebSockets offer performance and UX benefits, they also introduce security risks, especially due to:
- Long-lived connections
- Lack of built-in authentication
- Non-visibility in standard security appliances
5. WebSocket Attack Surface
WebSockets change the traditional threat model. Let’s understand the vulnerabilities.
1. Cross-Site WebSocket Hijacking (CSWSH)
If a WebSocket server trusts the Origin header blindly, an attacker can initiate a connection from a malicious page.
Mitigation:
- Always validate the Origin header on the server side
- Implement CSRF protection mechanisms
2. Lack of Authentication
WebSocket handshakes occur over HTTP, but the session may be upgraded without reauthentication.
Mitigation:
- Require authentication tokens in the initial handshake
- Tie WebSocket sessions to user sessions securely
3. Insecure WebSocket Endpoints
Using unencrypted ws:// protocol can expose traffic to Man-in-the-Middle (MitM) attacks.
Mitigation:
- Always use wss:// (WebSocket over TLS)
- Ensure TLS certificates are up to date
4. Input Validation
WebSockets are often not behind Web Application Firewalls (WAFs), making them a blind spot for security teams.
Mitigation:
- Enforce input validation on both client and server
- Integrate WebSocket traffic inspection in IDS/IPS
6. WebSocket Pentesting Techniques
For penetration testing engineers, WebSockets require specialised tools and techniques.
A. Interception Proxies
Use Burp Suite or ZAP with WebSocket support to intercept traffic.
B. Manual Frame Manipulation
Manually inject payloads into frames to test for:
- SQLi
- XSS
- Command Injection
- Insecure deserialisation
C. Fuzzing WebSocket Parameters
Fuzz input values in JSON or binary frames for overflow and logic flaws.
D. Origin Spoofing
Try initiating connections from different origins to test Origin validation.
E. Rate Limiting and DoS Testing
Flood with ping frames or malformed binary data to test server resilience.
7. WebSocket Pentest Checklist
| Test Category | Checklist Item |
| Handshake | Validate Origin header |
| Authentication | Verify token/session binding |
| Transport Security | Use wss:// and strong TLS |
| Input Validation | Fuzz message body |
| Rate Limiting | Check for DoS via flood |
| Session Management | Test session expiry/reuse |
| Authorisation | Try horizontal/vertical privilege escalation |
| Logging & Monitoring | Ensure activity is auditable |
8. Developer Best Practices for Secure WebSocket Implementation
- Enforce HTTPS-only Connections: Always prefer wss://.
- Session Validation: Re-check user authentication at every new WebSocket session.
- Rate Limiting: Set maximum concurrent connections and message size limits.
- Input Sanitisation: Use robust schema validation (e.g., JSON schema).
- Secure Headers: Set proper Origin checks and CORS headers.
- Logging: Log important events such as handshake failures and disconnections.
- Timeouts and Keep-alives: Detect and kill stale sessions.
- Monitoring: Use network anomaly detection systems to analyse persistent connections.
9. Real-World Incidents Involving WebSockets
1. Slack Token Exposure
Slack used WebSockets to transmit user tokens. An attacker intercepted the token through an insecure browser extension, gaining access to sensitive user data.
2. Crypto Trading Platforms
Some exchanges used unvalidated WebSocket payloads for trade execution, allowing unauthorised trade initiation through session hijacking.
3. Healthcare Chatbots
A vulnerability in WebSocket sessions allowed enumeration of past patient records due to poor access control logic.
10. Business Impact of Poor WebSocket Security
A. Financial Risk
An exploited WebSocket can result in data breaches, fraud, or unauthorised transactions.
B. Reputation Damage
Real-time services are expected to be secure. A breach erodes user trust quickly.
C. Compliance Violation
If PII or health data is transmitted over insecure channels, organisations may face fines under GDPR, HIPAA, or DPDP Act (India).
D. Operational Downtime
WebSocket-based DoS attacks can cripple real-time apps, affecting customer support or trading platforms.
11. WebSockets and ROI: The C-Suite Perspective
Pros:
- Enhances real-time capability and UX
- Reduces backend polling overhead
- Increases customer satisfaction
Cons (If Insecure):
- High cost of breach response
- Downtime and business disruption
- Legal and regulatory penalties
ROI comes from balancing performance with proactive security.
12. The Future of WebSocket Security
Emerging Solutions:
- WebSocket-aware WAFs: Modern WAFs now offer WebSocket inspection.
- ML-based Anomaly Detection: Models that learn WebSocket usage patterns to detect anomalies.
- Zero Trust Architectures: Treat every WebSocket request as untrusted until verified.
Integration with CTEM
WebSockets must be part of Continuous Threat Exposure Management (CTEM) pipelines for proactive threat modelling.
13. Final Thoughts: Closing the Loop Between Developers and Security Teams
WebSockets bridge the gap between innovation and usability—but only when used securely. For developers, understanding the protocol inside out leads to better design decisions. For penetration testers, mastering the WebSocket threat surface reveals powerful entry points often overlooked in traditional testing.
For C-level executives, investing in WebSocket security awareness, tooling, and testing offers long-term ROI, risk reduction, and customer trust.
Final Insights
WebSockets are not just a protocol—they’re a paradigm shift in how the web communicates. As businesses race to deliver instant, immersive experiences, WebSocket security must be treated as a boardroom priority, not just a developer concern.
Security is no longer about perimeter firewalls and antivirus software. It’s about defending every live connection—every open socket—with discipline, foresight, and collaboration.