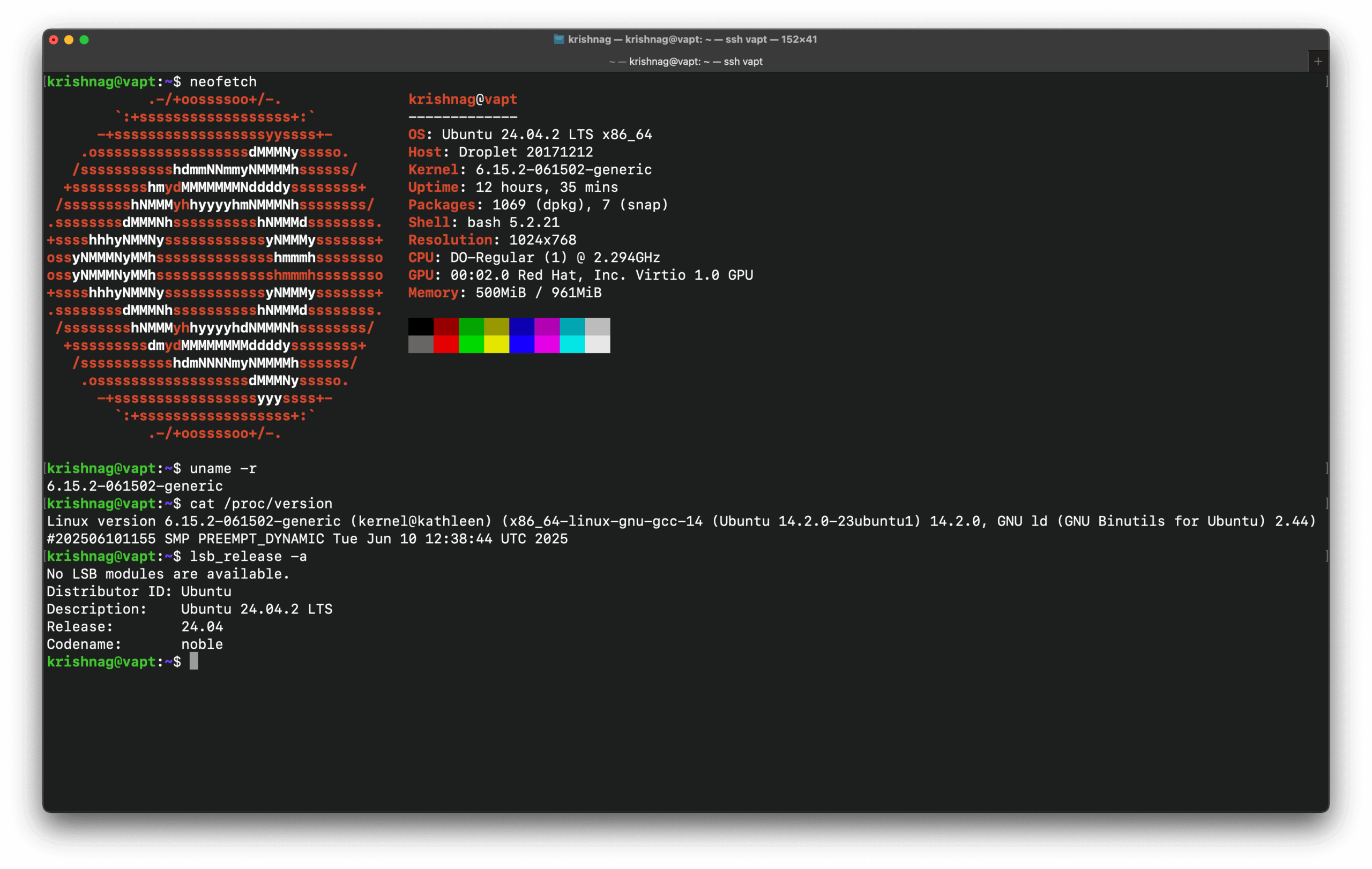
Upgrading Ubuntu Kernel v6.15.2
🔐 Linux Kernel v6.15 – What’s New & Security-Relevant
🗓️ Released: 26 May 2025
(With follow-up patches v6.15.1 and v6.15.2)
🗓️ Released: v16.15.2 on 10th June 2025
1. 🛡️ Security Enhancements
🔸 LSM (Linux Security Modules) Improvements
- Landlock expanded to support
truncate,link, andrenameoperations — improving sandboxing capabilities. - Support for stackable LSMs enhanced, allowing
AppArmorandSELinuxto co-exist with Landlock in more use cases. - New hooks added to increase coverage of filesystem and IPC operations.
🔸 Spectre/Meltdown Updates
- Improved Speculative Store Bypass mitigation on newer AMD and Intel CPUs.
- New controls to force-disable speculation for specific processes, reducing attack surface.
🔸 Kernel Address Space Layout Randomisation (KASLR)
- Entropy quality improved; KASLR re-randomises more aggressively at runtime (experimental).
- CONFIG_RANDOMIZE_KSTACK_OFFSET improvements reduce kernel stack info leaks.
2. 🔗 Networking Security Upgrades
🔸 TCP/UDP Hardening
- More robust handling of IP fragmentation and edge-case TCP headers (mitigating DoS conditions).
- Added protections against TFO (TCP Fast Open) abuse.
🔸 Netfilter/iptables/nftables
- nftables now supports hash maps in hardware offload, accelerating firewall performance.
- Improved audit logging for dropped or malformed packets in netfilter.
🔸 XDP & eBPF
- eBPF verifier hardened further against privilege escalation bugs.
- XDP (eXpress Data Path) gets better program chaining support, allowing more modular packet inspection — useful for next-gen IDS/IPS.
3. 🔒 Memory & Process Protection
- Rust-based Kernel Modules: Although still limited, the infrastructure for safe systems-level coding expands.
- Stack and heap memory poisoning (post-free detection) improved for slab caches — increasing resistance to use-after-free exploits.
- Userfaultfd interface made safer and more predictable — often used in fuzzing environments.
4. 📦 Filesystem & Storage Security
- fs-verity improvements: now supports large metadata and custom hashing — useful for software attestation and malware-resistant boot paths.
- Btrfs, Ext4, and XFS get improved journaling and recovery capabilities (less risk in crash scenarios).
- Better sandboxing support when mounting filesystems in user namespaces.
5. 🧠 Virtualisation & Containerisation
- Enhanced isolation for KVM guests:
- vmgenid support added for better snapshot detection (anti-cloning protection).
- VirtIO enhancements reduce data leakage between host/guest.
- Cgroups v2 gets new resource limits and syscall restrictions — improving container security profiles.
- LXC and systemd-nspawn get more stable under newer namespaces.
6. 🔧 Developer & Security Tooling
- Kprobes and ftrace performance boosted, reducing noise in syscall tracing.
- More stable
perfevent grouping — important for malware detection through behavioural profiling. - Kernel symbol export restrictions tightened to prevent exploit kits from abusing debug interfaces.
📊 Summary Table
| Feature Area | Key Improvements | Security Impact |
|---|---|---|
| LSM | Expanded Landlock, Stackable LSMs | Stronger sandboxing, RBAC/ABAC |
| eBPF & XDP | Safer verifier, better chaining | Safer packet inspection |
| Networking | Hardened TCP/UDP stack, better netfilter logs | Reduced DoS, improved traceability |
| Memory Management | Poisoning, KASLR entropy | UAF & info leak mitigation |
| Virtualisation | vmgenid, cgroup syscall limits | Container/VM boundary protection |
| Filesystem | fs-verity extended | Anti-tamper assurance |
🧩 For SecureMinds
- Easier to sandbox security tools using Landlock or cgroups.
- Improved network telemetry via eBPF helps in agentless VAPT.
- Safer environments for running kernel fuzzers, exploit research, or malware sandboxes.
- Upgraded memory and process protections directly reduce risks of local privilege escalation in red team setups.
From the kernel version listing, here is a summary of the Ubuntu Kernel v6.15 development and release timeline:
🧪 Development Milestones:
- v6.15-rc1: 2025-04-14
- v6.15-rc2: 2025-04-14
- v6.15-rc3: 2025-04-20
- v6.15-rc4: 2025-04-28
- v6.15-rc6: 2025-05-13
- v6.15-rc7: 2025-05-18
(It seems rc5 is either skipped or not listed here.)
✅ Stable Release:
- v6.15: 2025-05-26
🛠 Patch Releases:
- v6.15.1: 2025-06-04
- v6.15.2: 2025-06-10
📈 Next Release Series:
- v6.16-rc1: 2025-06-08
- v6.16-rc2: 2025-06-15
I am currently using Linux kernel v6.13, while the latest available stable version is v6.15.2 (as of 2025-06-10), with v6.16-rc2 already in testing.
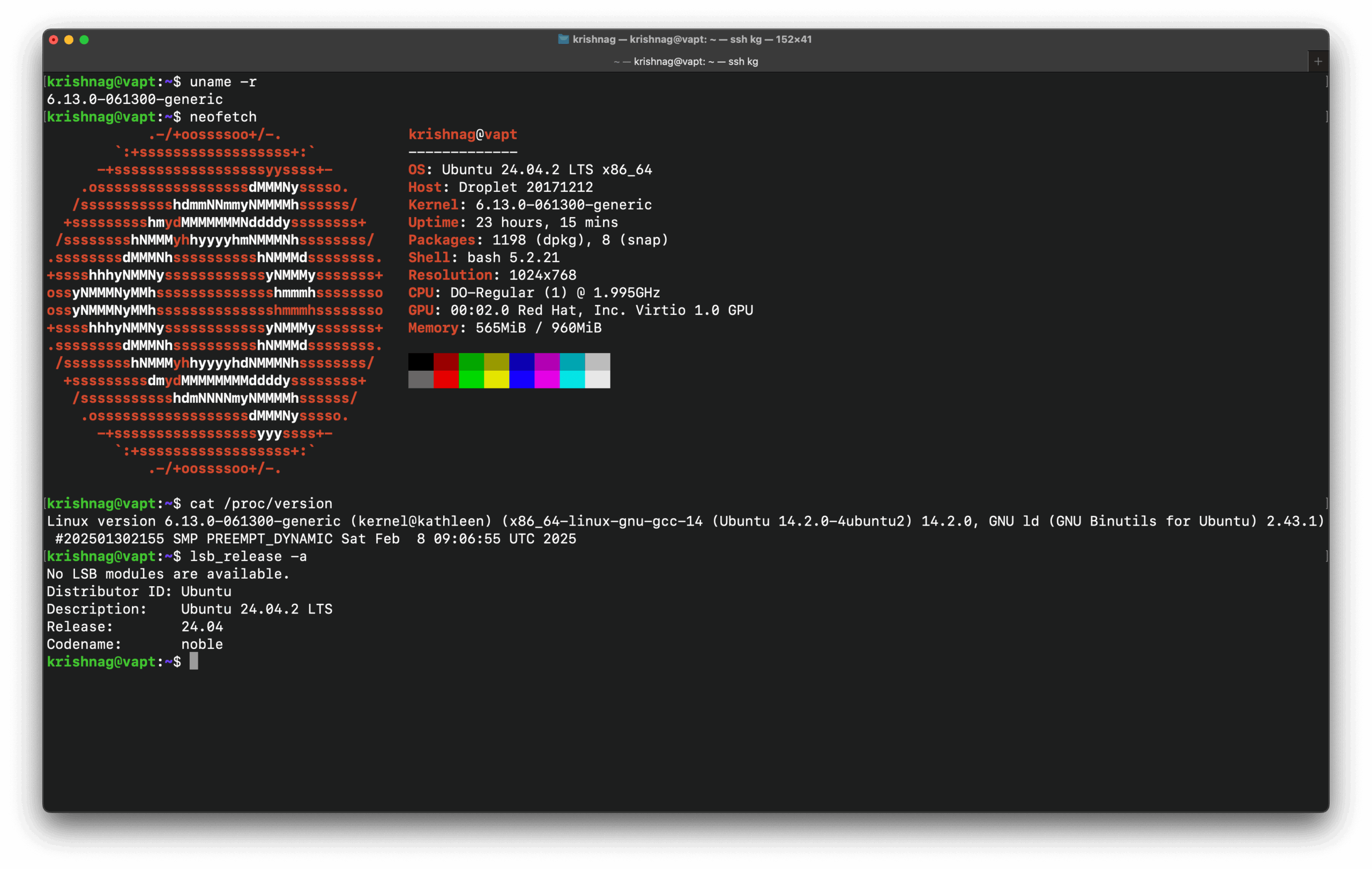
Here’s a quick comparison and why upgrading may be beneficial or necessary, especially for security-conscious environments:
🔒 Security & Stability:
- v6.13 is now two stable versions behind, which means:
- You’re missing several CVE patches fixed in v6.14 and v6.15.
- Security modules (like SELinux, AppArmor, Landlock) and eBPF-based hardening have received important updates since v6.13.
🚀 Key Improvements from v6.13 → v6.15:
| Area | What’s New or Improved |
| Networking | Performance optimisations for TCP & UDP stacks, better IPv6 handling, improved XDP (eXpress Data Path) support |
| Filesystem | btrfs, ext4, and XFS improvements; lower latency; fs-verity support enhancements |
| Security | Landlock LSM expanded, Spectre/Meltdown mitigations tightened, Kernel Stack Offset Randomisation (KASLR) improvements |
| Hardware Support | Broader support for newer AMD, Intel, and ARM SoCs (especially RISC-V); improved GPU and NVMe support |
| Performance | Lower syscall overhead, enhanced scheduler tuning for server loads |
| AI/ML | Kernel optimisations for AI workloads, including Intel AMX, AMD XDNA support added in later RCs of 6.15 |
✅ Should You Upgrade?
If you’re running:
- Production servers handling sensitive data
- Security testing environments
- Workstations needing latest hardware support
Then upgrading to v6.15.2 (latest stable) or tracking v6.16 RCs is strongly recommended.
🧩 How to Upgrade on Ubuntu:
If you’re using Ubuntu’s mainline kernels:
# Download and install using Ubuntu Mainline Kernel Installer:
sudo add-apt-repository ppa:cappelikan/ppa
sudo apt update
sudo apt install mainline
Then open the mainline GUI and install v6.15.2 or newer.
Or manually:
# For AMD64 architecture (example)
wget <https://kernel.ubuntu.com/~kernel-ppa/mainline/v6.15.2/>…
sudo dpkg -i *.deb
The v6.15.2 (not 16.5.2), based on the kernel versioning is stable.
✅ Is Linux Kernel v6.15.2 Stable?
Yes, v6.15.2 is a stable release. It is a point release built on top of the main v6.15 kernel, incorporating:
- Security patches
- Bug fixes
- Minor hardware or driver updates
These updates are released after v6.15 was declared stable on 26 May 2025, and v6.15.2 on 10 June 2025, following testing and regression checks.
🔍 How Stable is it in Production?
- 🧪 Stability Rating: As of now, v6.15.2 is production-grade stable — especially on well-supported platforms (Intel, AMD64, and ARM64).
- 🛡️ Security-Focused: Includes patches for CVEs found after 6.15.1.
- 🧰 Driver Maturity: Most major hardware drivers have matured by .2 release.
- ⚙️ Enterprise Use: Many organisations (especially in performance or security-focused contexts) wait until .2 or .3 before deploying a new kernel.
🛑 Considerations Before Upgrading:
- Compatibility with proprietary drivers (e.g., NVIDIA, ZFS DKMS, or VPN modules).
- eBPF-based agents (e.g., CrowdStrike, Falco) may require revalidation.
- Production environment should ideally test it first in staging or CI pipelines.
🔄 Recommendation for You :
Since you’re running potentially kernel-exploiting tools, v6.15.2 gives:
- Improved syscall tracing
- Better support for eBPF/XDP (important for modern recon tools)
- Tightened LSM enforcement
- More robust protection for containers and namespaces
In short: If you’re not bound by LTS constraints (like 6.1 or 5.15 LTS), then v6.15.2 is a solid, stable upgrade path.
However, for ultra-critical workloads, wait until v6.15.3 or use v6.14.x if maximum maturity is preferred.
✅ v6.15.2 is a solid, stable upgrade path
If:
- You’re not strictly tied to LTS kernels like 6.1 or 5.15
- You need newer hardware support, enhanced eBPF/networking, or security fixes
- You’re working in cutting-edge testing, VAPT, or research environments (like OMVAPT does)
❗ Stick with LTS (6.1 / 5.15) only if:
- You require ultra-long support cycles
- Your toolchains, drivers, or client infra are validated only against LTS
Here is a professional-grade Kernel Upgrade Checklist tailored for environments like OMVAPT where security, stability, and tool compatibility are essential:
✅ Kernel Upgrade Checklist (for Ubuntu or Debian-based systems)
📁 1. Pre-Upgrade Preparation
[ ] Confirm Current Kernel:
uname -r && lsb_release -a
[ ] Check Existing Kernel Packages:
dpkg –list | grep linux-image
- [ ] Backup Important Data & Configs
- /etc/fstab, /boot/grub/, /etc/network/interfaces (if used)
- Create a disk snapshot or VM snapshot if in cloud or virtualised environments.
[ ] List Custom Kernel Modules:
lsmod > ~/kernel_modules_backup.txt
[ ] Document Active DKMS Modules (e.g., NVIDIA, ZFS, WireGuard):
dkms status
📦 2. Download & Install New Kernel
- [ ] Choose Stable or LTS Kernel:
Use Ubuntu Kernel PPA or mainline tool.
[ ] Install mainline GUI Tool (optional):
sudo add-apt-repository ppa:cappelikan/ppa
sudo apt update && sudo apt install mainline
- [ ] OR manually download .deb packages for:
- linux-headers-xxx
- linux-modules-xxx
- linux-image-xxx
And install:
sudo dpkg -i *.deb
🧪 3. Validation Before Reboot
[ ] Confirm kernel is installed:
dpkg –list | grep linux-image
[ ] Update GRUB (if needed):
sudo update-grub
[ ] Set Default Kernel (if multiple):
Edit /etc/default/grub and adjust GRUB_DEFAULT or use:
sudo grub-set-default 0
🔁 4. Reboot & Switch
[ ] Reboot System:
sudo reboot
[ ] Verify Booted Kernel:
uname -r
🛠 5. Post-Upgrade Checks
[ ] Check system logs:
dmesg | less
journalctl -xe
[ ] Rebuild/reinstall DKMS modules (if applicable):
sudo dkms autoinstall
- [ ] Validate Firewall Rules, AppArmor, SELinux (if used)
- [ ] Run a full VAPT toolset validation (Metasploit, Nmap, Burp Suite, etc.)
- [ ] Test production services / agents (e.g., Zabbix, CrowdStrike, Wazuh)
💡 6. Rollback Plan (Just in Case)
- [ ] Keep at least one older stable kernel installed
- [ ] Use GRUB boot menu to select older kernel if boot fails
- [ ] Use Live USB Rescue Mode if system is unbootable
- [ ] Maintain remote console (iDRAC, iLO, or cloud serial console) if headless
🧩 Bonus: Automation & Audit
- [ ] Document the upgrade (who, when, why, version)
- [ ] Use Ansible or shell scripts to replicate on other servers
- [ ] Notify stakeholders about the upgrade window & result
Below is a robust, professional fallback & recovery plan tailored for your infrastructure in case something breaks after a Linux kernel upgrade.
🔄 Kernel Upgrade Fallback & Recovery Plan
🎯 Objective
To ensure minimal downtime, system recoverability, and business continuity in case the new kernel version causes:
- Boot failure
- Driver/module incompatibility
- Service disruption
- Toolchain malfunction (e.g., Burp, Metasploit, VPN, ZAP)
✅ 1. Pre-Fallback Safety Measures
Execute these before upgrading the kernel.
[ ] Retain at least one previous working kernel version
dpkg –list | grep linux-image
- If not, install an older kernel manually as a fallback.
[ ] Enable GRUB Menu at boot:
Edit /etc/default/grub:
GRUB_TIMEOUT_STYLE=menu
GRUB_TIMEOUT=5
Then:
sudo update-grub
- [ ] Create a Bootable Rescue Disk or Live USB
Use Ubuntu Desktop ISO or Rescue tools like SystemRescueCD - [ ] Ensure remote access failsafe:
- Cloud: Enable Serial Console Access
- Bare Metal: iDRAC/iLO or BMC access
- VM: Enable virtual console and snapshot
- [ ] Snapshot the system (if virtualised or cloud):
- AWS: AMI or EBS snapshot
- Proxmox/VMware: Use built-in snapshot feature
- AWS: AMI or EBS snapshot
LVM: Create snapshot:
lvcreate –size 1G –snapshot –name root_snap /dev/mapper/ubuntu–vg-root
⚠️ 2. Post-Upgrade Failure Scenarios & Fixes
🛑 A. System Fails to Boot
- Press Esc or Shift at boot → GRUB menu
- Select older working kernel (e.g., 6.13.x)
If it boots:
sudo apt purge linux-image-6.15.2
sudo update-grub
🛠 B. Kernel Modules Fail to Load (e.g., NVIDIA, WireGuard, ZFS)
Boot into recovery or terminal:
sudo dkms autoinstall
sudo modprobe <module-name>
Reinstall affected DKMS modules:
sudo apt install –reinstall <module-dkms-package>
🧹 C. Networking Issues (e.g., no IP, missing interfaces)
- Check ip link or ifconfig
- Revert netplan or networkd configs if touched
- Use Live CD to restore /etc/network/interfaces or /etc/netplan/*.yaml
🔄 D. GRUB Corruption
- Boot into Live CD
Mount system:
sudo mount /dev/sdaX /mnt
sudo mount –bind /dev /mnt/dev && sudo chroot /mnt
grub-install /dev/sda
update-grub
exit
reboot
♻️ 3. Full Kernel Rollback Steps
Only needed if partial fixes fail.
- Boot into previous stable kernel
Remove the faulty one:
sudo apt purge linux-image-6.15.2 linux-headers-6.15.2
sudo update-grub
Lock to known good version:
sudo apt-mark hold linux-image-6.13.0-xx
🧾 4. Documentation & Recovery SOP
- Maintain a Kernel Change Log (date, version, reason, outcome)
- Define owner responsible for kernel rollbacks
- Store Live ISO and rescue credentials securely
- Setup a “Post-Kernel-Upgrade Validation Script” to auto-check:
- Network up?
- System logs clean?
- Kernel modules loaded?

🧠 What is a Kernel in UNIX/Linux?
The kernel is the core component of a UNIX/Linux operating system. It works as a bridge between the hardware and user-space applications, managing system resources, hardware communication, and process execution.
🧩 Key Roles of the Kernel
1. Resource Manager
- Manages CPU time, RAM, I/O devices, and storage.
- Ensures fair and secure distribution of resources among processes.
2. Process Management
- Handles process creation, scheduling, execution, and termination.
- Supports multitasking, allowing multiple programs to run simultaneously.
3. Memory Management
- Allocates and deallocates memory safely and efficiently.
- Implements techniques like virtual memory, paging, and swapping.
4. Device Management
- Uses device drivers to interact with hardware (e.g., disks, keyboards, network cards).
- Provides a unified API so software can work with hardware abstractly.
5. File System Management
- Provides an interface to store, access, and manage files.
- Supports multiple file systems like ext4, XFS, Btrfs, etc.
6. Security & Isolation
- Implements user permissions, capabilities, and Linux Security Modules (LSM) like AppArmor, SELinux, and Landlock.
- Controls access to system resources via syscalls and namespaces.
🔍 Kernel Architecture in Linux
Types of Kernels:
- Monolithic Kernel (like Linux): All core services run in kernel space for performance.
- Microkernel: Only basic services run in kernel space, rest in user space (more modular but can be slower).
Linux follows a modular monolithic approach, supporting loadable kernel modules (LKMs) that can be added/removed without rebooting.
📦 Why the Kernel Matters in Cybersecurity and VAPT
- A vulnerable kernel can be exploited for privilege escalation or kernel-mode rootkits.
- VAPT tools often rely on kernel syscalls, tracing, and network stacks.
- Secure kernels ensure stronger system isolation and better attack surface control.
📘 Example (User ↔ Kernel Interaction):
When you run:
cat /etc/passwd
catmakes a system call to the kernel.- The kernel reads the file from disk and passes it back to
cat. - You see the result in your terminal — but it’s the kernel doing the real work under the hood.