A Comprehensive Guide to VPN Protocols for Information Security Architects
In an era where digital transformation is rapidly reshaping business operations, protecting data during transmission has become paramount. Virtual Private Network (VPN) protocols are pivotal in safeguarding sensitive information as it traverses public networks. This blog post explores the intricacies of VPN protocols, their significance, advantages, and challenges, providing Information Security Architects with the insights needed to make informed decisions that align with business goals.
Understanding VPN Protocols
What Are VPN Protocols?
A VPN protocol is a set of rules and encryption standards that determine how data is securely transmitted between a user’s device and the VPN server. These protocols ensure confidentiality, integrity, and authenticity, critical pillars of secure communication.
VPN protocols are the backbone of any VPN service, influencing the performance, security, and compatibility of the network. Choosing the right protocol is vital for achieving a balance between speed, security, and reliability.
Key VPN Protocols and Their Features
1. Point-to-Point Tunnelling Protocol (PPTP)
- Overview: Developed by Microsoft in the mid-1990s, PPTP is one of the earliest VPN protocols.
- Security: While PPTP is easy to set up and widely supported, its encryption standards (MS-CHAP-v2) are outdated, making it susceptible to attacks.
- Performance: High speed due to low encryption overhead, making it suitable for streaming and non-critical tasks.
- Use Cases: Legacy systems or scenarios where speed is prioritised over security.
2. Layer 2 Tunnelling Protocol (L2TP)/IPsec
- Overview: L2TP, combined with IPsec, enhances security by encrypting data packets and ensuring their integrity.
- Security: Strong encryption (AES-256) and authentication mechanisms.
- Performance: Slightly slower due to double encapsulation but provides robust protection.
- Use Cases: Secure remote access for businesses requiring a balance between security and performance.
3. Secure Socket Tunnelling Protocol (SSTP)
- Overview: A Microsoft-developed protocol that operates over port 443, easily bypassing firewalls.
- Security: Uses SSL/TLS encryption, ensuring secure and tamper-resistant communication.
- Performance: Reliable and less prone to blockage but limited to Windows environments.
- Use Cases: Enterprises operating within a Microsoft ecosystem.
4. OpenVPN
- Overview: Open-source and highly configurable, OpenVPN is the gold standard for VPN protocols.
- Security: Utilises SSL/TLS for encryption, with support for strong ciphers like AES-256.
- Performance: Flexible; offers UDP (faster) and TCP (more reliable) modes.
- Use Cases: Businesses prioritising security and flexibility across multiple platforms.
5. Internet Key Exchange Version 2 (IKEv2)/IPsec
- Overview: Jointly developed by Microsoft and Cisco, IKEv2 is known for its stability and mobility support.
- Security: Robust encryption, offering resistance against certain attack vectors.
- Performance: Fast and efficient, particularly on mobile networks.
- Use Cases: Mobile devices and applications requiring seamless reconnection.
6. WireGuard
- Overview: A modern, lightweight protocol designed for simplicity and efficiency.
- Security: Utilises state-of-the-art cryptography with a small codebase, reducing the risk of vulnerabilities.
- Performance: Exceptional speed due to streamlined architecture.
- Use Cases: Scenarios requiring high performance and scalability, such as cloud infrastructure.
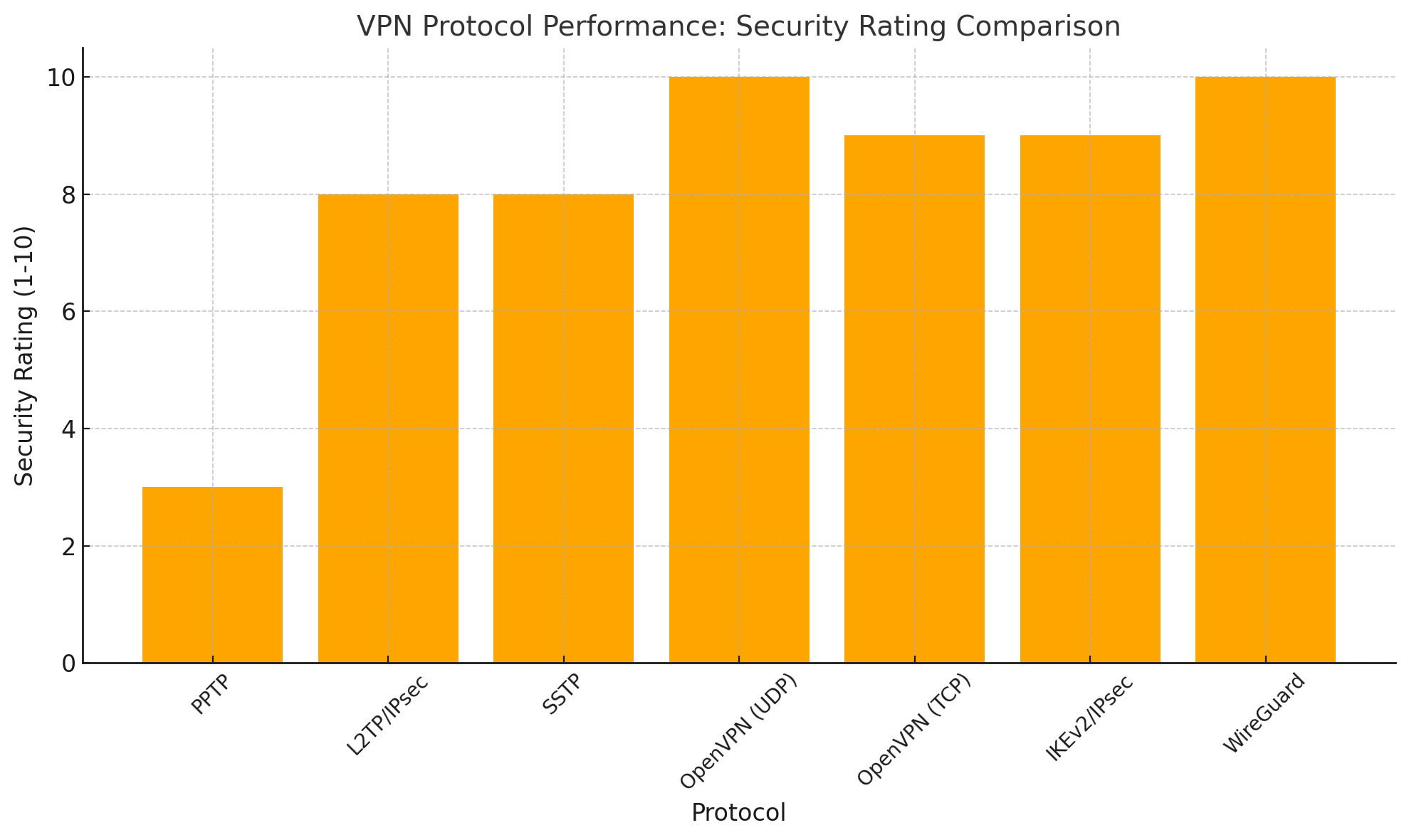
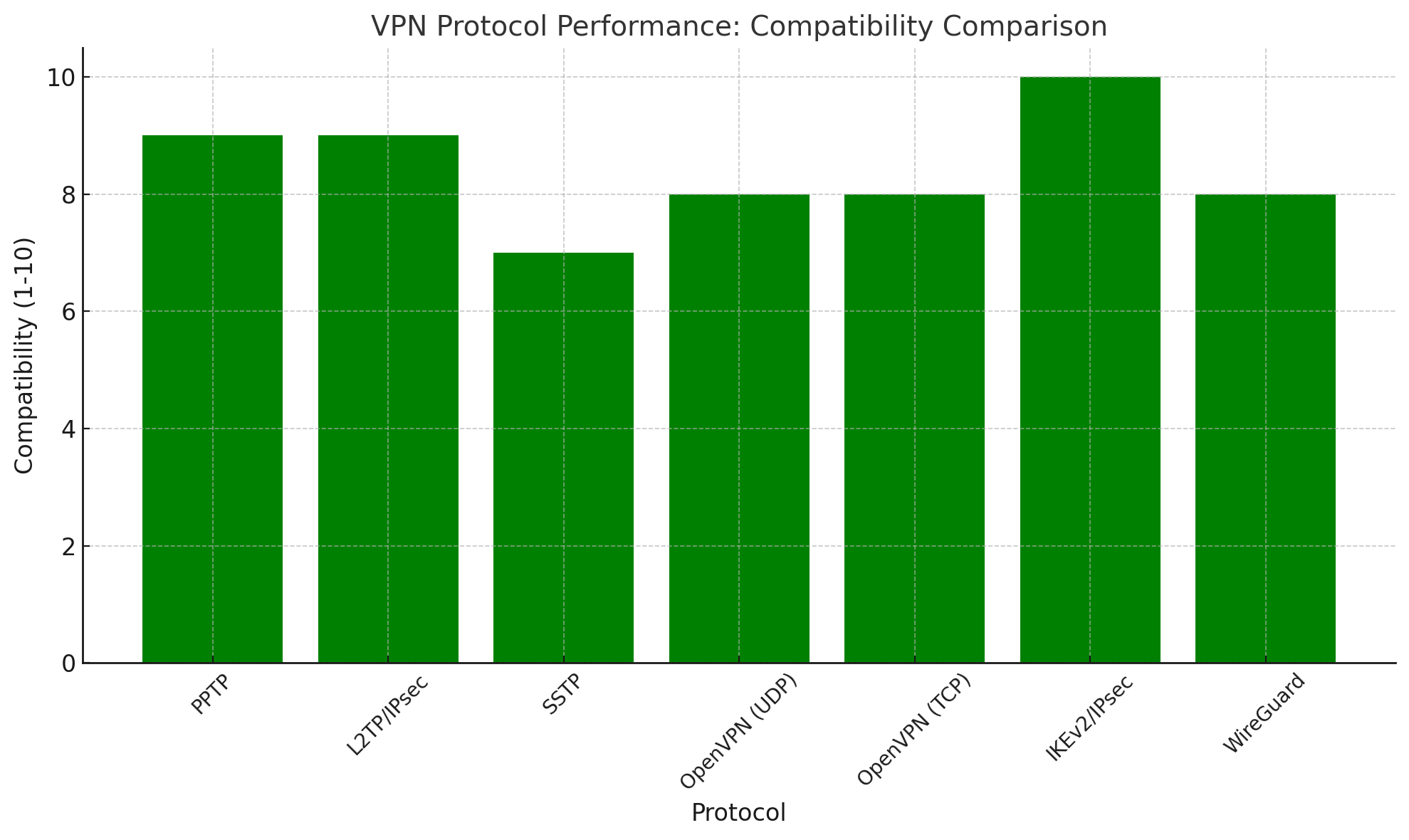
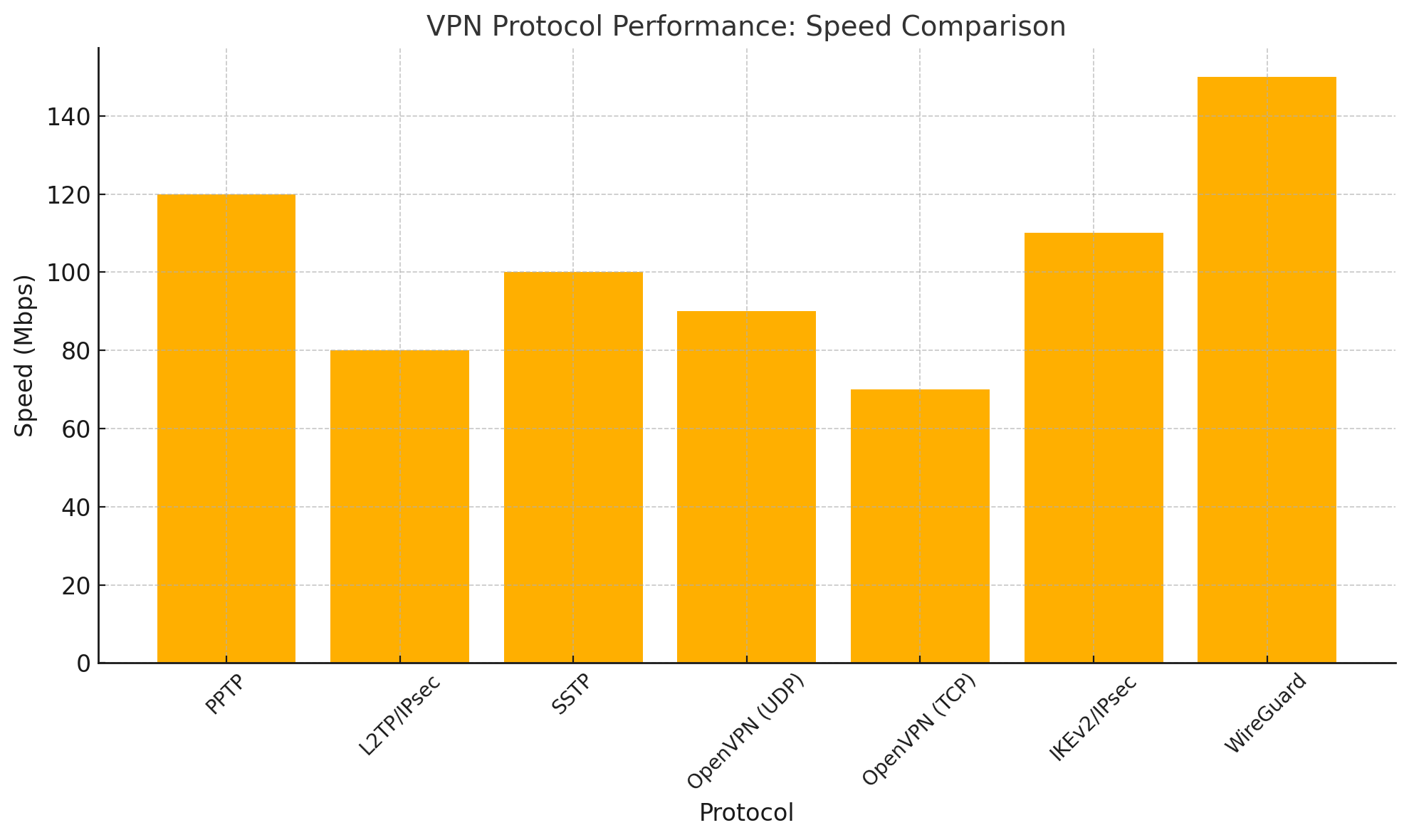
Comparative Analysis of VPN Protocols
| Protocol | Security | Performance | Compatibility | Best Use Cases |
|---|---|---|---|---|
| PPTP | Low | High | High | Legacy systems |
| L2TP/IPsec | High | Moderate | High | Business use |
| SSTP | High | Moderate | Windows-centric | Microsoft ecosystems |
| OpenVPN | Very High | Customisable | High | Security-focused tasks |
| IKEv2/IPsec | High | High | High | Mobile applications |
| WireGuard | Very High | Very High | Growing | High-performance environments |
Selecting the Right Protocol: A Strategic Approach
Factors to Consider
- Security Requirements: Organisations dealing with sensitive data, such as financial services, should prioritise protocols like OpenVPN or IKEv2/IPsec.
- Performance Needs: Industries requiring low-latency communication, such as online gaming, may favour WireGuard.
- Compatibility: Ensure the chosen protocol aligns with existing infrastructure and device ecosystems.
- Compliance Standards: Adhere to regulatory requirements such as GDPR, HIPAA, or PCI-DSS when selecting protocols.
- Scalability: Consider future growth and the ability of the protocol to adapt to evolving business needs.
Real-World Applications and Case Studies
Case Study 1: Enhancing Security for Remote Work
A multinational corporation transitioned to a hybrid work model during the pandemic. By implementing OpenVPN, they achieved a secure, scalable solution, safeguarding sensitive communications and ensuring compliance with GDPR.
Case Study 2: Streamlining Mobile Connectivity
A fintech company adopted IKEv2/IPsec to support its mobile workforce, providing seamless connectivity and robust security, even in low-bandwidth environments.
Emerging Trends in VPN Protocols
1. Integration with Zero Trust Architectures
VPNs are evolving to complement Zero Trust frameworks, prioritising granular access controls and continuous monitoring.
2. Quantum-Resistant Encryption
With quantum computing on the horizon, protocols incorporating quantum-resistant algorithms are under development to future-proof VPNs.
3. Hybrid Protocols
Combining the strengths of multiple protocols, hybrid solutions are emerging to deliver superior performance and security.
WireGuard VPN Protocol: A Modern Marvel
WireGuard has revolutionised the VPN landscape with its simplicity, speed, and robust security. Unlike traditional protocols that often prioritise either security or performance, WireGuard achieves a near-perfect balance of both. Designed with modern cryptographic principles, it addresses the shortcomings of legacy protocols like IPsec and OpenVPN.
Overview of WireGuard
WireGuard is a cutting-edge VPN protocol developed by Jason A. Donenfeld. Initially released in 2017, it was designed to offer a lightweight, fast, and secure alternative to existing protocols. The protocol has gained widespread adoption due to its efficiency and ability to meet the demands of contemporary networking environments.
Key Features of WireGuard
- Modern Cryptography
- WireGuard employs state-of-the-art cryptographic algorithms, including:
- ChaCha20 for encryption
- Poly1305 for data authentication
- Curve25519 for key exchange
- BLAKE2 for hashing
- These algorithms ensure security while maintaining computational efficiency.
- WireGuard employs state-of-the-art cryptographic algorithms, including:
- Simplicity
- The protocol has a compact codebase of approximately 4,000 lines, significantly smaller than OpenVPN or IPsec. This minimises vulnerabilities and makes auditing easier.
- Performance
- WireGuard outperforms many legacy protocols due to its streamlined design. It reduces overhead and latency, resulting in faster speeds, even on resource-constrained devices.
- Cross-Platform Compatibility
- WireGuard supports various operating systems, including:
- Linux (native support integrated into the Linux kernel)
- macOS
- Windows
- iOS
- Android
- WireGuard supports various operating systems, including:
- Ease of Configuration
- WireGuard uses static IP addresses and public/private key pairs, simplifying setup and management compared to certificate-based protocols like IPsec.
How WireGuard Works
WireGuard operates at the network layer (Layer 3 of the OSI model) and uses a peer-to-peer model. Here’s how it works:
- Key Exchange:
- Each peer generates a pair of public and private keys. These keys are exchanged securely and used to establish encrypted tunnels.
- Tunnel Establishment:
- Once keys are exchanged, a tunnel is created between peers. Each peer has a static IP address within the virtual private network.
- Packet Encryption:
- Data packets are encrypted using ChaCha20, ensuring confidentiality and integrity.
- Routing:
- WireGuard routes traffic through the encrypted tunnel based on preconfigured IP ranges.
Advantages of WireGuard
- Speed:
- WireGuard is optimised for performance, often doubling or tripling the throughput of older protocols like OpenVPN and IPsec.
- Security:
- Its use of modern cryptographic primitives ensures resistance to known vulnerabilities.
- The minimal codebase reduces the attack surface.
- Efficiency:
- Low resource consumption makes WireGuard suitable for devices with limited computational power, such as IoT devices and mobile phones.
- Flexibility:
- WireGuard’s cross-platform support and simplicity make it an excellent choice for diverse network environments, including enterprise and cloud deployments.
- Future-Proofing:
- WireGuard is designed to adapt to new cryptographic standards as they emerge, ensuring long-term viability.
Does WireGuard uses IPv6?
Yes, WireGuard fully supports IPv6, both for transport (the underlying network) and within the VPN tunnel itself. Here’s how IPv6 is utilised in WireGuard:
1. Transport Layer Support
WireGuard can operate over IPv6 networks, meaning the VPN server and client can communicate using IPv6 addresses as the underlying transport layer. This is particularly useful in modern networks where IPv6 adoption is increasing due to the depletion of IPv4 addresses.
2. Tunnel Layer Support
WireGuard can also route IPv6 traffic through the VPN tunnel. For example:
- The VPN tunnel itself can be assigned an IPv6 address.
- Devices within the WireGuard network can communicate with each other using IPv6.
- It can handle both IPv4 and IPv6 traffic simultaneously (dual-stack support).
Why IPv6 is Important for WireGuard
- Future-Proofing: As IPv6 adoption grows, having a VPN protocol that seamlessly supports it ensures long-term compatibility.
- Increased Address Space: IPv6 provides a virtually unlimited number of unique IP addresses, which can simplify network configurations in complex environments.
- Improved Efficiency: IPv6 eliminates the need for Network Address Translation (NAT), simplifying communication between devices in certain scenarios.
By supporting IPv6 natively, WireGuard ensures compatibility with modern networking environments and positions itself as a forward-looking VPN solution.
Does WireGuard supports IPv4?
Yes, WireGuard fully supports IPv4 in addition to IPv6. It is designed to work seamlessly in both IPv4 and IPv6 environments, making it a versatile choice for a wide range of networking scenarios.
How WireGuard Uses IPv4
- Transport Layer:
- WireGuard can operate over IPv4 networks, meaning the communication between the VPN client and server can use IPv4 addresses.
- This is particularly useful in networks that do not yet support IPv6 or are configured exclusively with IPv4.
- Tunnel Layer:
- WireGuard can route IPv4 traffic through the VPN tunnel.
- Devices connected to the WireGuard VPN can communicate with each other using IPv4 addresses within the virtual private network.
- Dual-Stack Support:
- WireGuard supports dual-stack configurations, meaning it can handle both IPv4 and IPv6 traffic simultaneously within the same tunnel.
- This allows for seamless operation in mixed network environments.
Why IPv4 Support Matters
- Global IPv4 Usage: While IPv6 adoption is growing, IPv4 remains the dominant protocol in many networks worldwide.
- Compatibility: Full support for IPv4 ensures WireGuard can be deployed in legacy systems and environments where IPv6 is unavailable.
- Flexibility: Supporting both IPv4 and IPv6 enables organisations to transition to IPv6 gradually without compromising on VPN functionality.
In summary, WireGuard’s support for IPv4 makes it a practical and compatible VPN solution for both current and emerging networking standards.
Challenges and Limitations
- Static IP Requirement:
- WireGuard’s reliance on static IPs for each peer may complicate dynamic network environments.
- No Built-in User Authentication:
- WireGuard does not natively support username/password authentication, relying solely on key pairs. This can necessitate additional measures for user management.
- Limited Support for Legacy Systems:
- WireGuard’s modern architecture is incompatible with older operating systems that lack kernel support.
- Auditing Challenges in Large Deployments:
- In complex environments, auditing and managing keys across numerous peers can become cumbersome.
Real-World Use Cases
- Cloud Networking:
- Organisations using cloud services like AWS or Azure can leverage WireGuard for secure and high-speed connections between on-premises systems and cloud resources.
- Remote Workforce Security:
- Businesses adopting hybrid work models can use WireGuard to provide remote employees with secure access to corporate networks.
- IoT Security:
- WireGuard’s lightweight design makes it ideal for securing communication between IoT devices and central servers.
- High-Performance Applications:
- Industries requiring low-latency connections, such as gaming or video streaming, benefit significantly from WireGuard’s speed and efficiency.
WireGuard vs Traditional Protocols
| Feature | WireGuard | OpenVPN | IPsec |
|---|---|---|---|
| Codebase | ~4,000 lines | ~600,000 lines | ~400,000 lines |
| Encryption | Modern | Moderate | Moderate |
| Speed | Very High | Moderate | High |
| Configuration | Simple | Complex | Complex |
| Resource Usage | Low | Moderate | High |
Tips for Information Security Architects
- Integration:
- Leverage WireGuard for hybrid cloud and on-premises environments to optimise performance and security.
- Complementary Measures:
- Use WireGuard alongside firewalls, intrusion detection systems, and Zero Trust principles for enhanced protection.
- Monitor Updates:
- Regularly update WireGuard implementations to benefit from the latest security enhancements.
- Employee Training:
- Ensure IT teams are trained in deploying and managing WireGuard effectively.
WireGuard represents the future of VPN protocols, combining simplicity, speed, and robust security. For Information Security Architects, its adoption can significantly enhance network performance while reducing administrative complexity. As organisations navigate an increasingly digital world, protocols like WireGuard are indispensable tools for protecting data and maintaining business continuity.
By understanding WireGuard’s features, advantages, and limitations, organisations can harness its full potential to meet today’s and tomorrow’s cybersecurity challenges.
Here’s a comprehensive table listing popular VPN services and the protocols they support:
| VPN Service | Supported Protocols | Notes |
|---|---|---|
| ExpressVPN | OpenVPN, IKEv2, L2TP/IPsec, Lightway | Lightway is ExpressVPN’s custom protocol optimised for speed and security. |
| NordVPN | OpenVPN, IKEv2/IPsec, NordLynx (WireGuard) | NordLynx is NordVPN’s implementation of WireGuard for enhanced performance. |
| Surfshark | OpenVPN, IKEv2/IPsec, WireGuard | Offers dual-stack support for IPv4 and IPv6. |
| CyberGhost | OpenVPN, IKEv2/IPsec, WireGuard, PPTP, L2TP/IPsec | User-friendly interface suitable for beginners. |
| ProtonVPN | OpenVPN, IKEv2/IPsec, WireGuard | Focused on privacy and security, based in Switzerland. |
| Private Internet Access (PIA) | OpenVPN, WireGuard | Offers extensive customisation options for advanced users. |
| Mullvad | WireGuard, OpenVPN | Privacy-focused with a simple pricing model and no user tracking. |
| TunnelBear | OpenVPN, IKEv2 | Known for its ease of use and lighthearted design. |
| VyprVPN | OpenVPN, IKEv2, WireGuard, Chameleon | Chameleon is a proprietary protocol designed to bypass VPN restrictions. |
| PureVPN | OpenVPN, IKEv2/IPsec, L2TP/IPsec, WireGuard | Supports a wide range of devices and offers extensive server options. |
| IPVanish | OpenVPN, IKEv2, WireGuard | Offers unlimited simultaneous connections. |
| Hotspot Shield | Catapult Hydra, OpenVPN, IKEv2 | Catapult Hydra is a proprietary protocol optimised for performance. |
Key Observations
- OpenVPN:
- Universally supported across nearly all major VPN providers.
- Known for its balance of security and performance.
- WireGuard:
- Rapidly gaining popularity due to its speed, efficiency, and modern cryptography.
- Many providers have adopted it as a default or an alternative to OpenVPN.
- IKEv2/IPsec:
- Favoured for mobile devices due to its ability to handle network switching seamlessly.
- Proprietary Protocols:
- Some VPNs, like ExpressVPN and Hotspot Shield, have developed custom protocols (e.g., Lightway, Catapult Hydra) to optimise for specific use cases like streaming or evading censorship.
This table can guide users and Information Security Architects in selecting VPN services based on the supported protocols and their specific requirements.
Practical Tips for Information Security Architects
- Regularly Update Protocols: Keep VPN software and protocols updated to mitigate vulnerabilities.
- Test Configurations: Conduct rigorous testing to optimise performance and security settings.
- Educate End-Users: Provide training to employees on the importance of secure VPN usage.
- Monitor Usage: Implement tools to monitor and analyse VPN traffic, ensuring compliance and detecting anomalies.
VPN protocols are a cornerstone of modern cybersecurity, enabling secure data transmission across diverse environments. Information Security Architects play a crucial role in selecting and implementing the right protocol to balance security, performance, and compatibility. By understanding the nuances of each protocol and staying abreast of emerging trends, organisations can bolster their defences and maintain a competitive edge.
Investing in the right VPN solution is not just a technical decision; it’s a strategic imperative with profound implications for business continuity, ROI, and risk mitigation. As the digital landscape evolves, so too must our approach to secure communication.
Cyber Attacks That Evade VPNs
While VPNs are powerful tools for enhancing online security and privacy, they are not invincible. Sophisticated cybercriminals can employ various techniques to bypass VPN protections and compromise user systems. Below is an exploration of common cyber attacks that can evade VPNs, including how they work and potential mitigation strategies.
1. Phishing Attacks
- How It Works:
- Attackers trick users into revealing sensitive information (e.g., credentials, financial data) through fake emails, websites, or messages.
- A VPN cannot protect users if they voluntarily provide their credentials to a malicious actor.
- Example: A phishing email disguised as a VPN provider asking users to “verify” their account.
- Mitigation:
- Educate users to recognise phishing attempts.
- Deploy anti-phishing software and email filtering systems.
2. Malware Infections
- How It Works:
- Malware can infiltrate devices through infected downloads, attachments, or compromised websites.
- Once installed, the malware can operate locally, stealing data or spying on the user, bypassing VPN protections.
- Example: A trojan that logs keystrokes or screenshots sensitive data, regardless of the VPN connection.
- Mitigation:
- Use endpoint protection tools.
- Regularly update software and operating systems to patch vulnerabilities.
3. Miscreants-in-the-Middle (MitM) Attacks
- How It Works:
- Attackers intercept communications between the user and the VPN server, potentially decrypting or altering the data.
- Weak encryption or misconfigured VPNs are particularly vulnerable.
- Example: A rogue Wi-Fi hotspot posing as a legitimate network to intercept VPN traffic.
- Mitigation:
- Use strong encryption protocols like AES-256.
- Enable Perfect Forward Secrecy (PFS) to ensure compromised session keys do not affect other sessions.
4. DNS Leaks
- How It Works:
- Even with a VPN, a device may send DNS queries outside the encrypted tunnel to the ISP’s DNS server, revealing browsing activity.
- Example: Accessing a website and inadvertently routing DNS requests through an unprotected ISP.
- Mitigation:
- Use a VPN with built-in DNS leak protection.
- Configure devices to use the VPN provider’s DNS servers.
5. Browser Fingerprinting
- How It Works:
- Websites can track users based on unique browser settings, extensions, and system configurations, bypassing VPN anonymity.
- Example: An attacker tracks user behaviour through JavaScript even when the VPN is active.
- Mitigation:
- Use privacy-focused browsers like Tor or Brave.
- Disable unnecessary plugins and extensions.
6. IP Address Leaks
- How It Works:
- VPNs may fail to mask the user’s real IP address due to technical issues or incorrect configuration.
- Certain websites or applications can exploit WebRTC to expose the user’s IP address.
- Example: A malicious website triggering a WebRTC request to reveal the actual IP address.
- Mitigation:
- Disable WebRTC in browser settings or use browser extensions to prevent leaks.
- Choose VPNs with strong leak protection mechanisms.
7. Social Engineering Attacks
- How It Works:
- Attackers manipulate users into bypassing their VPN or sharing sensitive information directly.
- Example: A phone call claiming to be from IT support asking the user to disable their VPN for troubleshooting.
- Mitigation:
- Conduct regular security training for employees.
- Establish clear policies against sharing credentials or disabling security tools without verification.
8. Advanced Persistent Threats (APTs)
- How It Works:
- Sophisticated, long-term cyberattacks target specific organisations, often combining multiple attack vectors.
- VPNs cannot protect against attackers who have already infiltrated internal systems.
- Example: A supply chain attack that introduces malicious software into the organisation’s network.
- Mitigation:
- Conduct regular security audits and penetration tests.
- Implement Zero Trust architectures to limit lateral movement.
9. VPN Exploits
- How It Works:
- Attackers exploit vulnerabilities in VPN software or protocols to gain unauthorised access.
- Example: Exploiting outdated versions of OpenVPN or misconfigured WireGuard setups.
- Mitigation:
- Regularly update VPN software and firmware.
- Monitor CVEs (Common Vulnerabilities and Exposures) related to VPN solutions.
10. Data Correlation Attacks
- How It Works:
- Even with a VPN, attackers can correlate metadata (e.g., connection times, IP addresses) from various sources to identify users.
- Example: A user’s VPN connection timestamps match activity on a monitored platform.
- Mitigation:
- Use VPNs with a strict no-logs policy.
- Combine VPNs with tools like Tor for enhanced anonymity.
Final Thoughts
VPNs are an essential component of modern cybersecurity, but they are not a silver bullet. Cybercriminals continue to innovate, finding ways to bypass VPN protections through social engineering, malware, and sophisticated attack vectors. For Information Security Architects, the key lies in adopting a layered security approach that integrates VPNs with other measures such as Zero Trust principles, endpoint security, and employee education.

By understanding these attack methods and implementing robust mitigation strategies, organisations can better protect their assets and maintain the trust of their stakeholders.